Hello there <!> In this article, I'll demonstrate how I discovered 3 1-Click Account Takeover vulnerabilities on the largest French Minecraft server: paladium-pvp.fr.
This Minecraft server was created in 2015 by YouTuber FuzeIII, who currently has 3.07 million subscribers.
The target scope was: *.paladium-pvp.fr
I found these vulnerabilities in just 5 minutes, so this will be a relatively short read (sorry about that!). However, the impact was critical since cookies were shared cross-domain.
Background
I used to play a lot on this server when I was younger, and I remembered that they had domains related to Discord, including a captcha bot verification system for every member joining the Discord server for the first time.
Initial Reconnaissance
For reconnaissance, I only used DNS Dumpster since I had an appointment scheduled an hour later and decided to do some quick testing while I had free time.
Those were the domains I found with DNS Dumpster.
Reflected XSS Leads to 1-Click ATO on *.paladium-pvp.fr
So, what happened with paladium-pvp.fr?
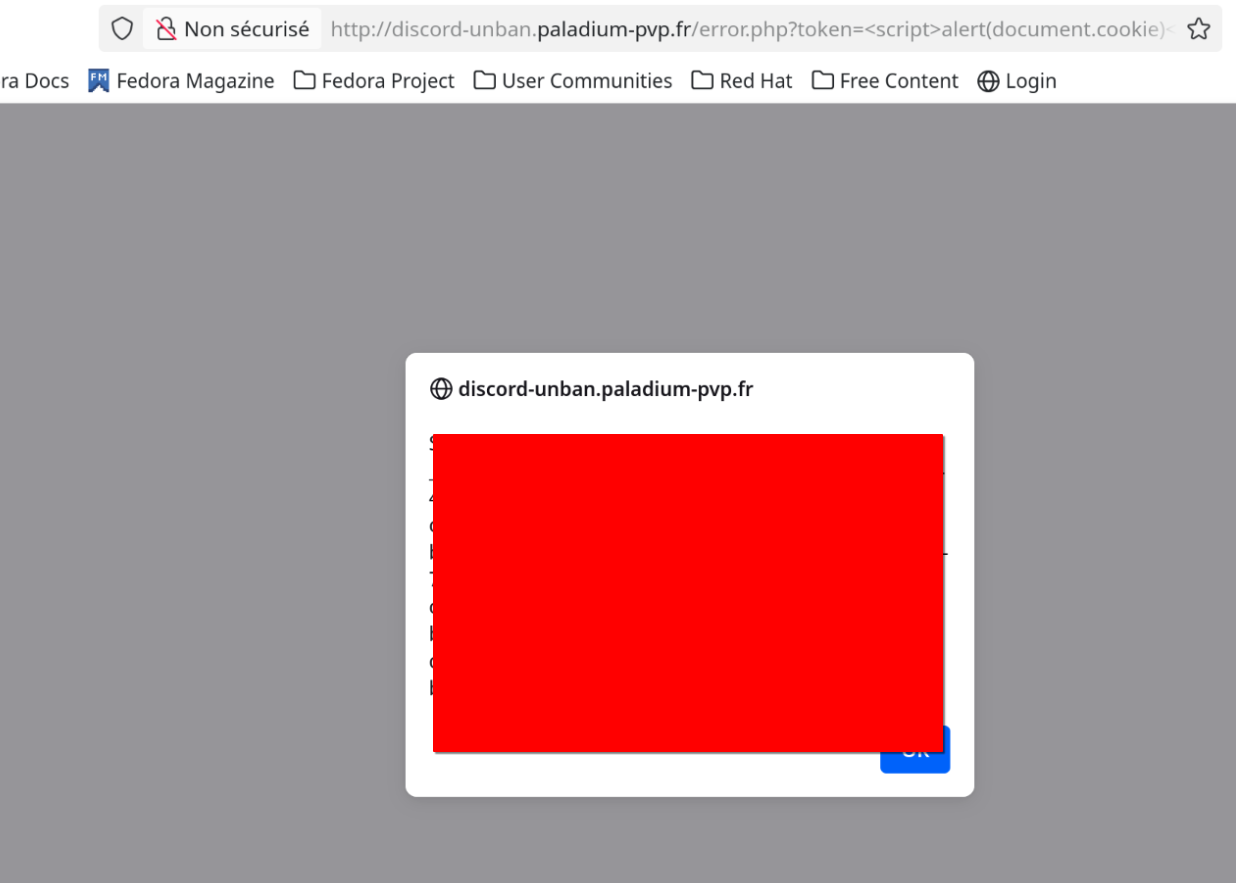
Well, I was curious about why there were 3 domains related to Discord, so I first visited discord-unban.paladium-pvp.fr and instantly got an error saying "Verification failed".
And I saw this:
The token parameter was reflected in the website's response, so I tried the most basic XSS payload and this happened:
The Other Two Vulnerabilities
Now you might be wondering: "That's cool, but where are the other two vulnerabilities?"
Well... remember those Discord subdomains I mentioned earlier?
Those domains were vulnerable in the exact same way! The vulnerable endpoint was: /error.php?token=XSS
How did I figure this out? All three domains shared the same design, so I suspected they were using the same codebase.
Unfortunately, I don't have screenshots of the other XSS vulnerabilities, but you can still visit the webpages (error 410 will pop up):
https://discord-unban.paladium-pvp.fr/https://discord.paladium-pvp.fr/https://discord-support.paladium-pvp.fr/
Disclosure
The vulnerabilities were responsibly disclosed to the Paladium team. Unfortunately, I didn't receive any acknowledgment for the findings :'(